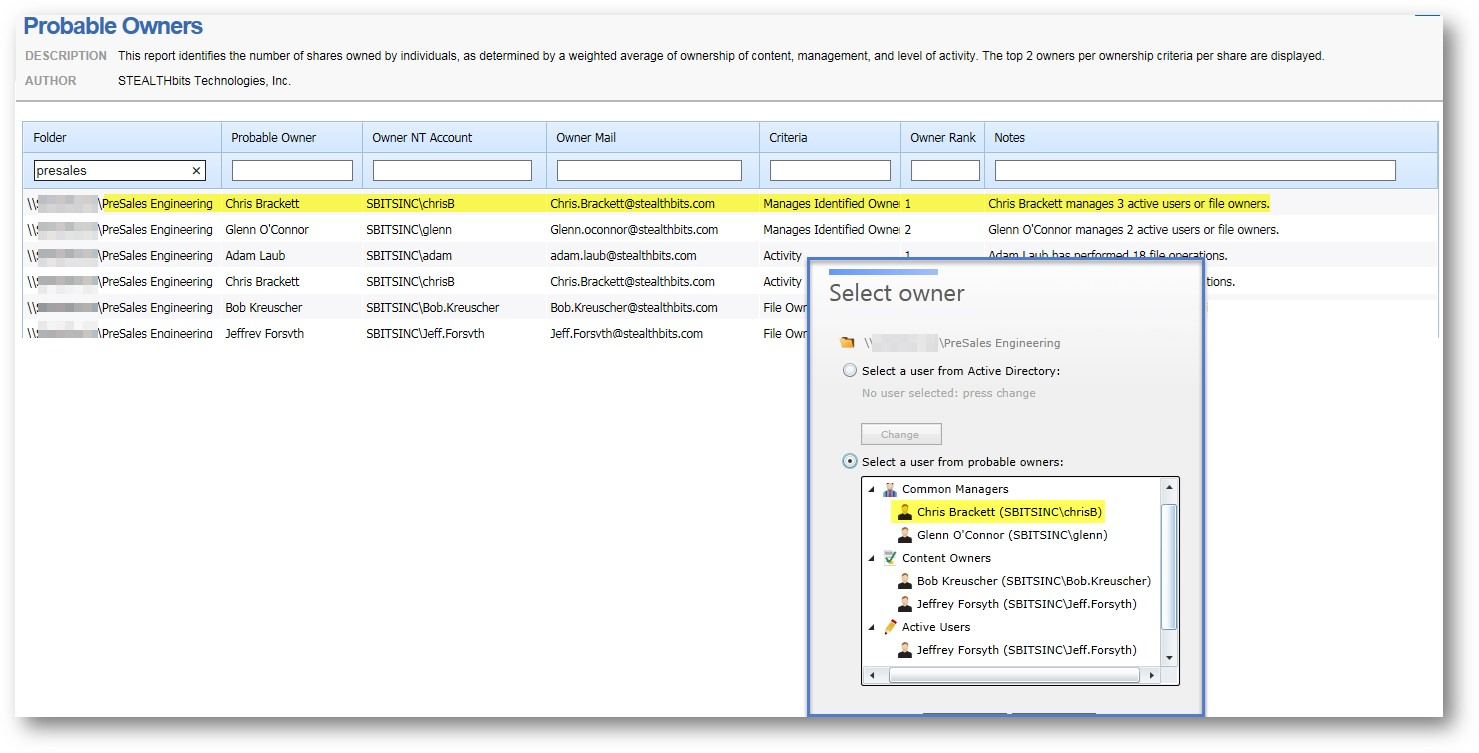
Ownership is key to beginning certification routines within your IAM platform of choice. StealthAUDIT can help you begin that process while onboarding a new IAM solution, or with existing solutions you may already have today. Right out of the box we can start identifying Probable Ownership within StealthAUDIT’s Report Index for both AD and unstructured data. The AD solution set shows probable owners for either security or distribution groups in the Probable Owners report (Active Directory > 1. Groups > Probable Owners); showing the best candidates based off existing ManageBy attributes of their respective members. The FileSystem Solution Set (FileSystem > 6. Probable Owner) and SharePoint Solution Set (SharePoint > 6. Probable Owner) show this as well using ranking for users that own the most data, managers of data owners, and even (with activity enabled) who the most active candidate is.
These probable owners can then be assigned to their respective resources within the Access Information Center’s “Manage Resource Ownership” option. Selecting “Add” in the lower left hand corner allows you to begin selecting desired resources and enumerates those same suggestions we saw within the Report Index for ownership (as shown below). Once selected, we have all the necessary information for your IAM to begin Group Certification or even bring Unstructured Data into your Identity and Access Management routines!
Don’t miss a post! Subscribe to The Insider Threat Security Blog here:




Leave a Reply