- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Stealthbits ProTip: Ransomware Detection with StealthINTERCEPT

Configure as follows:
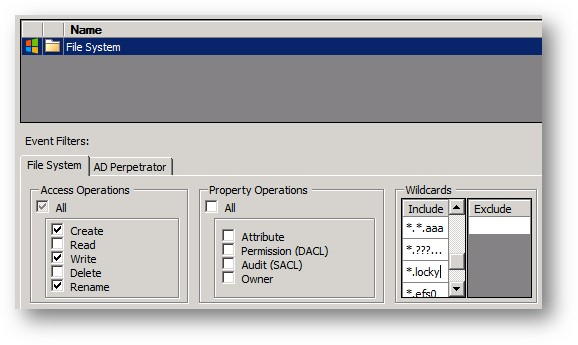
Set Access Operations to include Create, Write, and Rename (typically there will be a create operation from generating an encrypted copy, then subsequent destruction of the original in most attacks). And then enter desired Wildcards (* and ? can both be used) as follows:
- *.locky
- *.cryptolocker
- *.*.aaa
- Decrypt.me
There are many more that can be included and are as flexible as desired. The naming conventions can also be difficult to Wildcard at times. Fortunately, these criminals have one common factor and that’s MONEY. There will always be an instruction set on how to pay them, so any file being generated as Decrypt.me, Decrypt.Instructions, etc. can be another indicator of an attack.
As new attacks emerge, knowing that encryption naming convention makes it easy to update and add additional Wildcards. Having separate Policies is a great way to delineate between definite attacks and activity to review. With a properly scoped Policy, this is one of the few quick wins a security professional can have with immediately actionable information. Incorporating scripts, and integrating with an existing SIEM can further automate your protection/visibility to these Perpetrators.
Don’t miss a post! Subscribe to The Insider Threat Security Blog here:
Related Posts
- PROTIP – How to Purge Data in StealthAUDIT
- PROTIP – Fulfill a DSAR with StealthAUDIT 11.0
- Best Practices – Setting up StealthAUDIT SQL Server Database
- ProTip: How to Setup User Activity & Server Logon Scan in StealthAUDIT for Oracle
- Pro Tip – StealthINTERCEPT DB Maintenance Best Practices
- PROTIP: Policy Registration & Managing StealthINTERCEPT via PowerShell and Editing StealthDEFEND Investigations & Categorizing Playbooks
- PROTIP: How to Update the “Have I Been Pwned” (HIBP) Breach Dictionary in StealthINTERCEPT Enterprise Password Enforcer and StealthAUDIT
- Protip: How to Setup User Activity & Database Logon Scans in StealthAUDIT for Oracle
- ProTip – The Power of Character Substitution Checks in StealthINTERCEPT Enterprise Password Enforcer
- Protip: How to Setup User Activity & Server Logon Scan in StealthAUDIT for SQL
Featured Asset
Stealthbits Credential and Data Security Assessment
Proper data security begins with a strong foundation. Find out what you're standing on with a free deep-dive into the security of your Structured and Unstructured Data, Active Directory, and Windows infrastructure.
Read moreSubscribe
DON’T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.


Leave a Reply