End-to-End
Active Directory
Security Solution
Identify and mitigate security risks by performing Active Directory security assessment
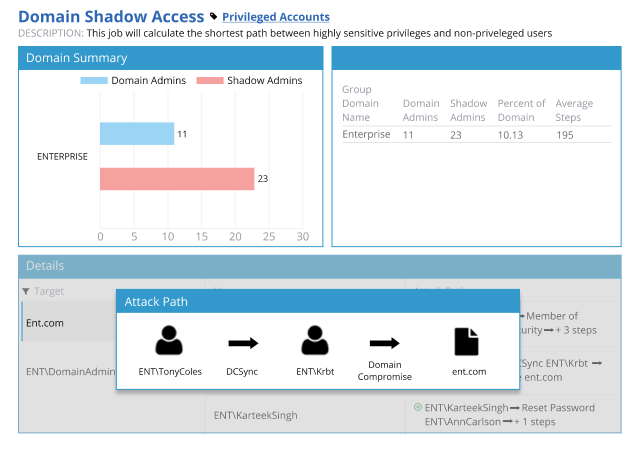
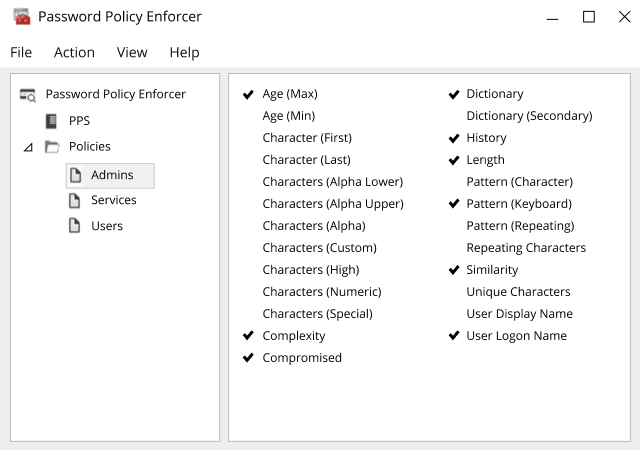
Active Directory is secure when it’s clean, understood, properly configured, closely monitored and tightly controlled. Netwrix Active Directory assessment tools make it easy to understand your current security posture and prioritize your risk mitigation efforts.
Rest assured your Active Directory is protected from security incidents
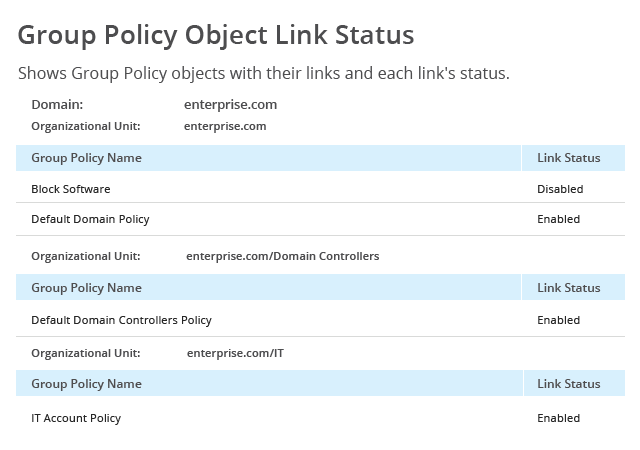
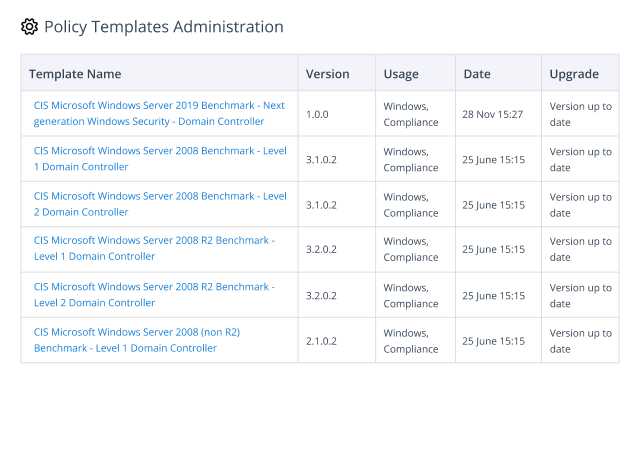
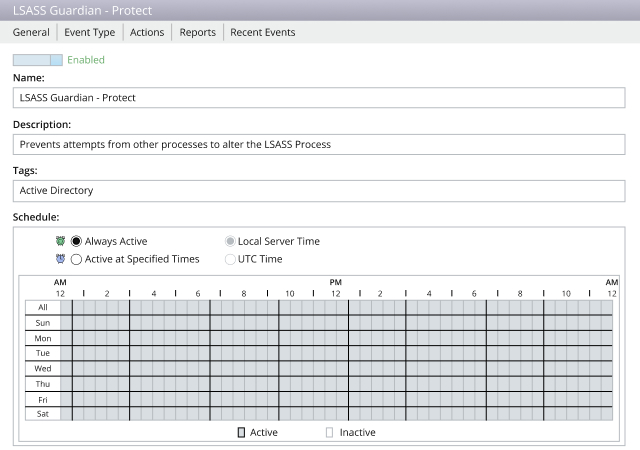
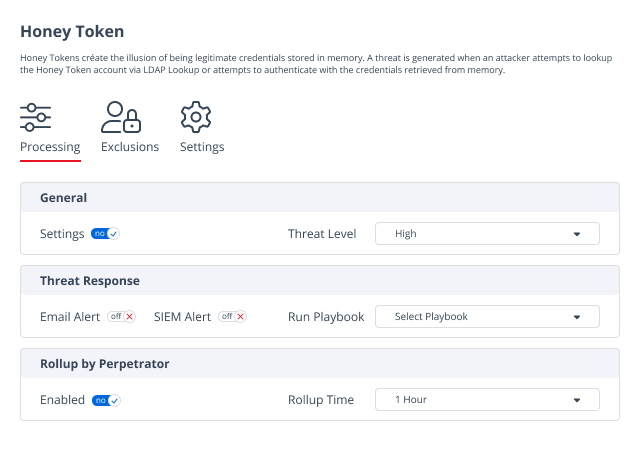
To minimize the risk of AD security breaches, organizations need to implement safeguards that protect Active Directory.
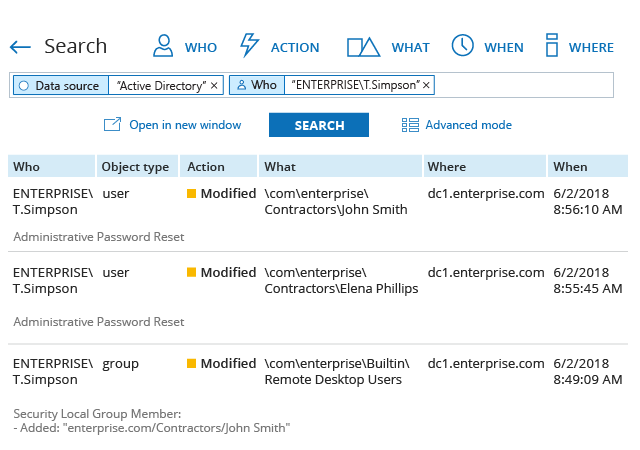
Be confident that you can spot threats in time to prevent a breach
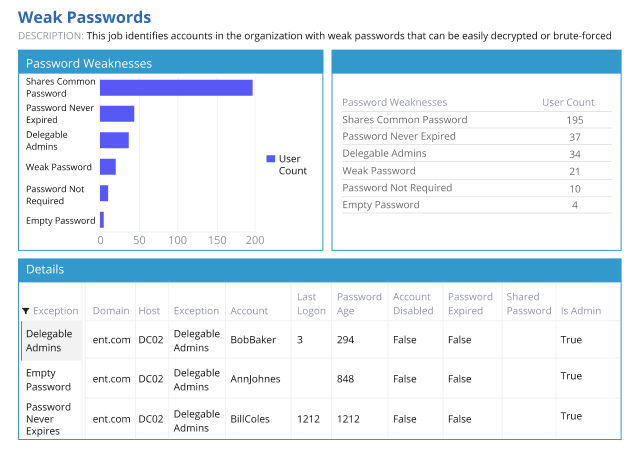
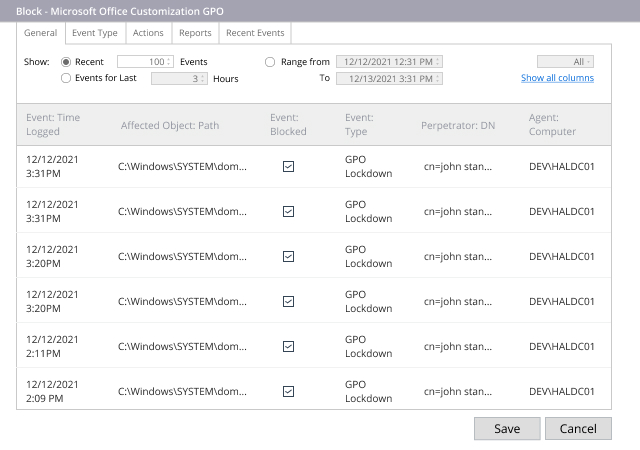
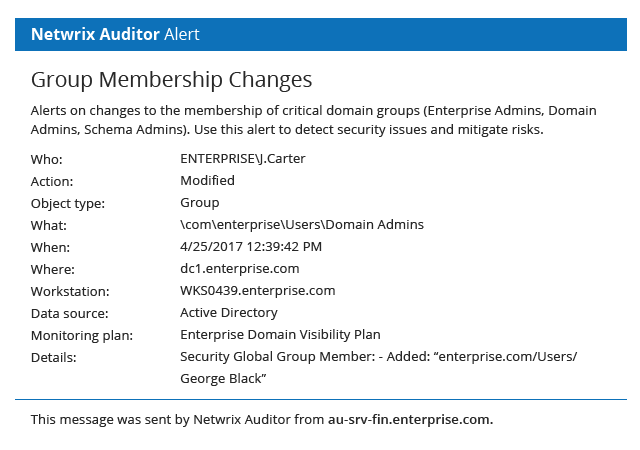
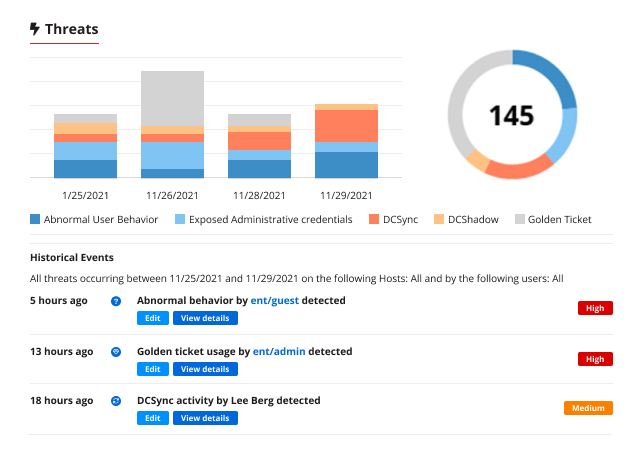
Because Active Directory is a mission-critical system, it is a prime target for adversaries. Ensure you can detect threats to Active Directory in time to prevent a devastating breach.
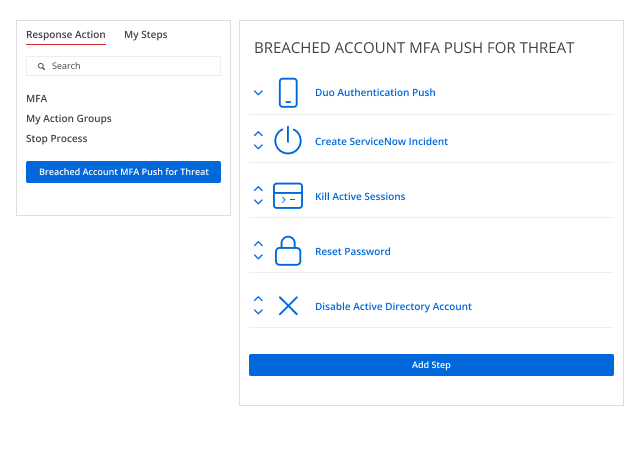
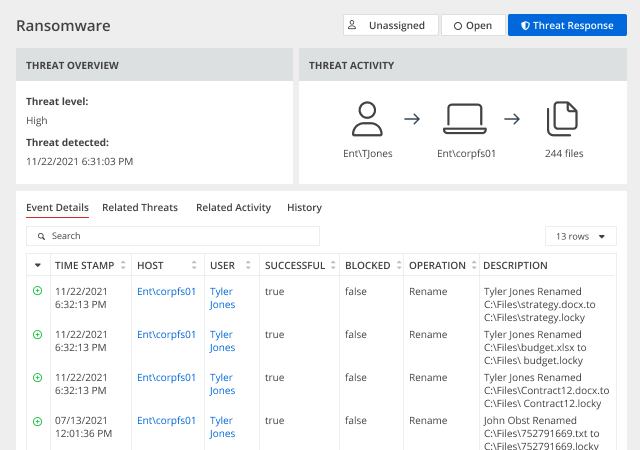
Save the day by mitigating the impact of Active Directory security incidents
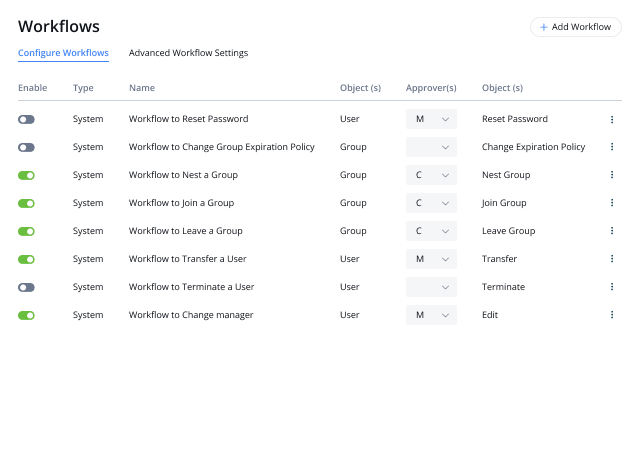
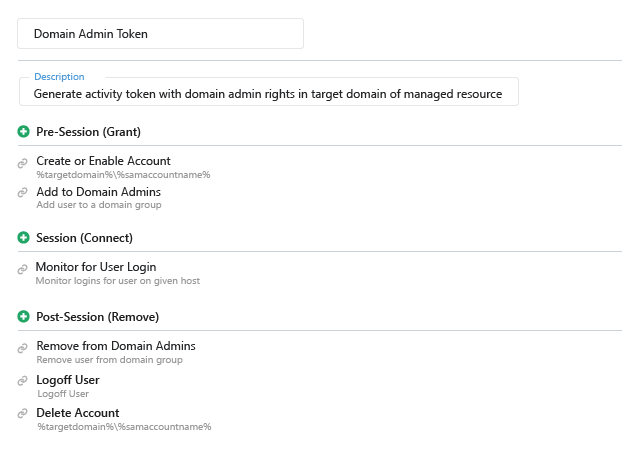
When an AD security incident occurs, every second counts. The Netwrix solution empowers security pros to respond quickly by providing actionable information — and even automating response to expected threats.
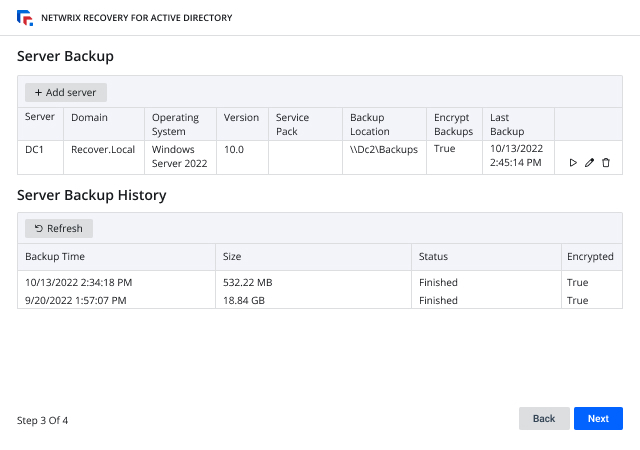
Be the hero by recovering from improper Active Directory changes quickly to ensure business continuity
Active Directory is critical to virtually all modern business operations, so quick AD recovery is vital. The Netwrix solution speeds rollback from unwanted AD changes and deletions and streamlines full domain recovery to ensure business continuity.

Security Solution

.jpg)