NETWRIX THREAT MANAGER (formerly Netwrix StealthDEFEND®)
catch complex attacks on the fly
Threat detection software from Netwrix to detect and respond to abnormal behavior and advanced attacks with high accuracy and speed
IT infrastructures are getting more complex and the volume of sensitive information stored there is skyrocketing. At the same time, the threat landscape is evolving rapidly, with attacks becoming more sophisticated and more costly. The question is not if your organization will be targeted, but when. How prepared are you to catch potential threats?
Detect threats and contain the damage across your most important systems
Active Directory
Windows File Servers
Dell Data Storage
NetApp
Nutanix Files
Qumulo
Nansuni
Panzura
Hitachi NAS
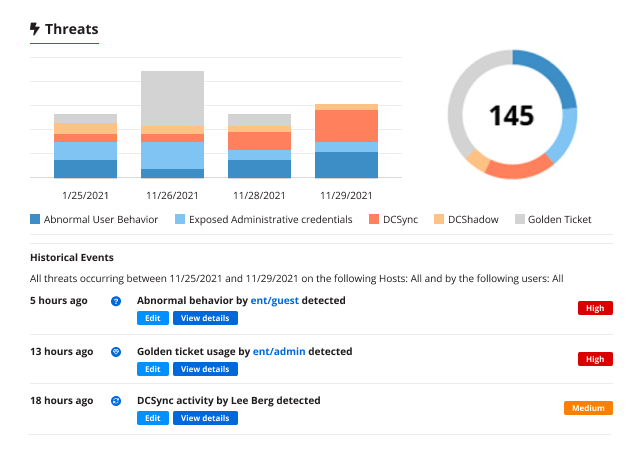
Minimize the time to detect and respond to complex security incidents
Real-time alerting
Improve your threat management processes and know about anything suspicious happening in your network, whether it’s an external attack or an insider threat, with real-time alerts delivered via email or mobile notifications,
Integration with other security technologies
Maximize the value of your investments and enhance security across the IT ecosystem by sharing data between Netwrix Threat Manager and your SIEM and other security solutions.
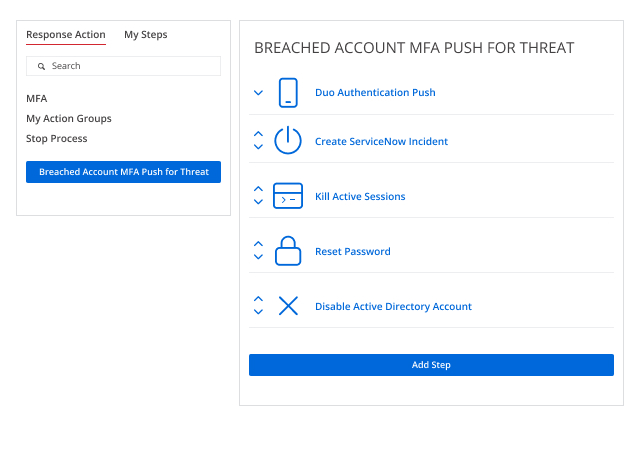
Automated response
Respond immediately upon threat detection by taking advantage of the extensive catalog of preconfigured response actions, or by integrating Netwrix Threat Manager with your own business processes using PowerShell or webhook facilities.
Machine learning and user behavior analytics
Fine-tune your threat detection by building profiles of normal user behavior and then monitoring and analyzing events to spot truly suspicious activity in the vast sea of user activity.
Deception tools
Enhance your threat intelligence by luring attackers into a honeypot where you can study their tactics and keep them away from your valuable assets. Built-in capabilities make deployment and management simple.
Auto-adjusting to risk behaviors
Automatically have your privileged users, groups, data and resources tagged as sensitive, so the ratings of security risk when abnormal behavior occurs around them get adjusted appropriately.
Comprehensive investigations
Easily gather the entire timeline of related events that comprised an attack to simplify investigation, threat analysis and recovery.
User-defined threats
Easily define threats specific to your organization or vertical. Reduce false positives by fine-tuning rules, logic and criteria to smoothly handle exclusions.
Datasheet
Netwrix Threat Manager
Find out how Netwrix can help you detect advanced attacks in real time and contain the damage.

What file system threats can Netwrix Threat Manager detect and respond to?
Netwrix Threat Manager can detect and respond to a number of file system threat models, including but not limited to:
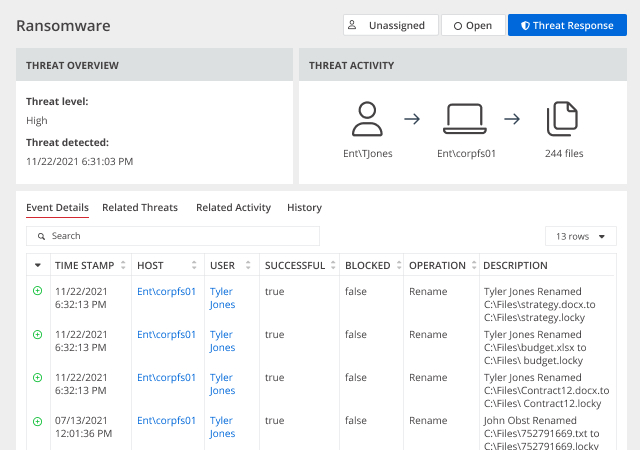
· Ransomware activity
· Abnormal user behavior
· Unusual sensitive data access
· Unusual process execution
· Data exfiltration attempts
· Mass file deletions
· First-time access
· Suspicious permission changes
· Abnormal denied activity
· Configuration file tampering
· Lateral movement
· Ransomware activity
· Abnormal user behavior
· Unusual sensitive data access
· Unusual process execution
· Data exfiltration attempts
· Mass file deletions
· First-time access
· Suspicious permission changes
· Abnormal denied activity
· Configuration file tampering
· Lateral movement
What Active Directory threats can Netwrix Threat Manager detect and respond to?
Netwrix Threat Manager can detect and respond to a number of Active Directory threat models, including but not limited to:
· DCShadow
· DCSync
· Golden Ticket
· Kerberoasting
· AS-REP Roasting
· LSASS process injection
· Password spraying
· Replication permissions tampering
· AdminSDHolder ACL tampering
· Pass-the-Ticket attacks
· Group Managed Service Account (GMSA) exploitation
· Forged PAC
· LDAP reconnaissance
· NTDS.dit, plaintext password extraction
· SID History tampering
· Anomalous authentications
· Hidden Object
· Service account misuse
· DCShadow
· DCSync
· Golden Ticket
· Kerberoasting
· AS-REP Roasting
· LSASS process injection
· Password spraying
· Replication permissions tampering
· AdminSDHolder ACL tampering
· Pass-the-Ticket attacks
· Group Managed Service Account (GMSA) exploitation
· Forged PAC
· LDAP reconnaissance
· NTDS.dit, plaintext password extraction
· SID History tampering
· Anomalous authentications
· Hidden Object
· Service account misuse
Is Netwrix Threat Manager secure?
Netwrix Threat Manager allows you to leverage any one-time password (OTP) solution supporting RADIUS for console access and configuration activities, so you can be sure the access to the console is secure.
What if I have a question or run into a problem?
Don’t worry! In case of non-technical questions about our products, simply contact your account manager. For technical issues, reach out to our U.S.-based customer support team, which has earned a solid 97% satisfaction rate.