Frustrate hackers, satisfy auditors and delight users with password policy enforcer from Netwrix
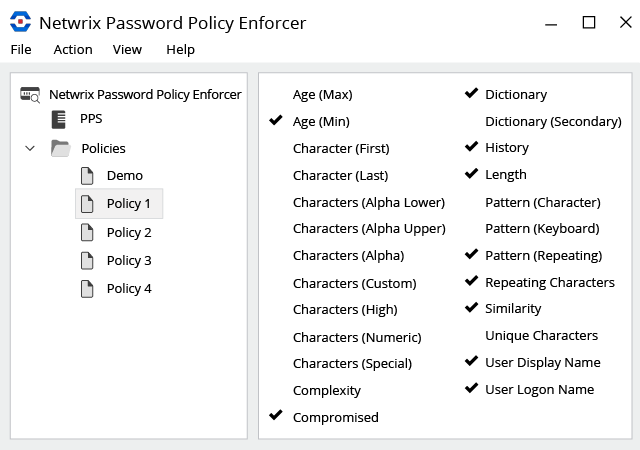
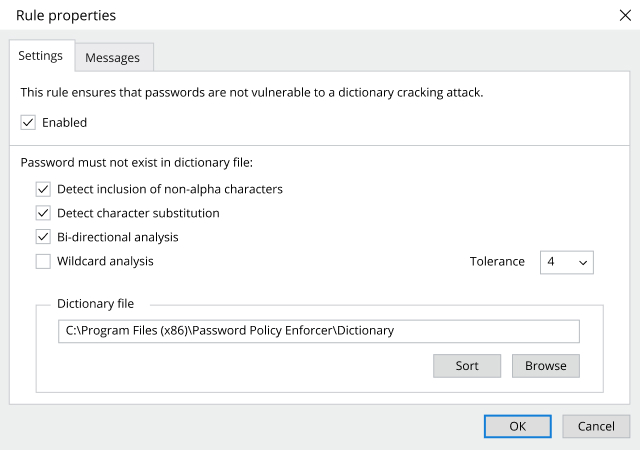
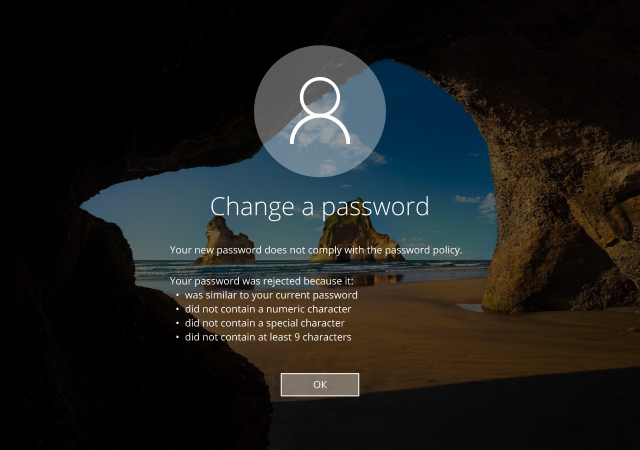
Leaked and weak passwords remain a gaping hole in IT networks, making it far too easy for attackers to gain the foothold they need to steal sensitive data, damage systems and unleash ransomware. Unfortunately, native Windows tools often cannot deliver the detailed configurations and rules required for modern password policies, leaving IT teams struggling to keep up with the changing threat landscape and evolving compliance requirements. Meanwhile, user productivity suffers and IT helpdesks are swamped as users grapple with unclear requirements for new passwords. Learn how Netwrix Password Policy Enforcer can help you achieve truly effective password enforcement without all the hassles.
Balance security and user productivity with a
flexible Active Directory password policy enforcer