Data Access Governance
Software to Lean On
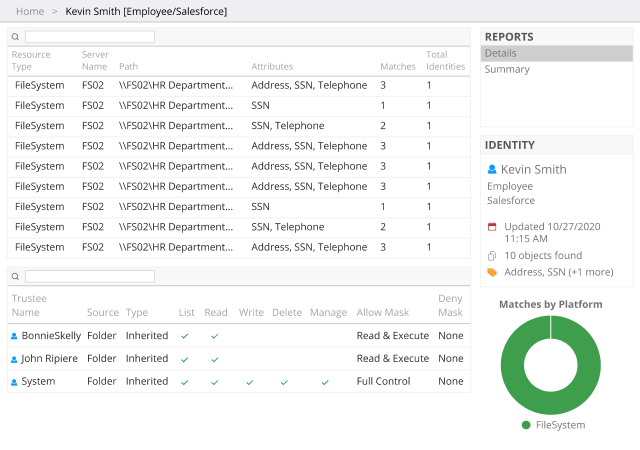
Expand your visibility into risks around sensitive data
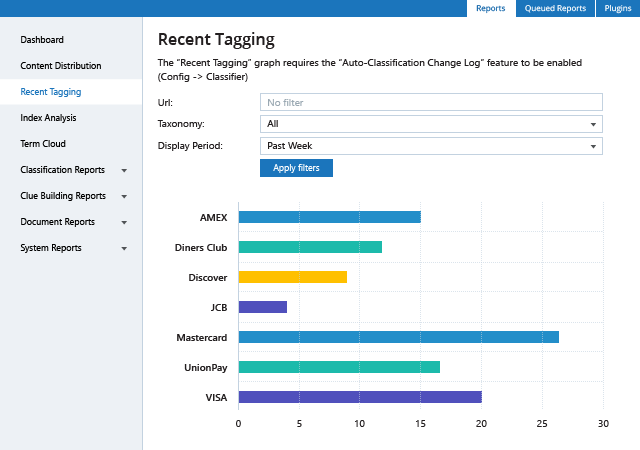
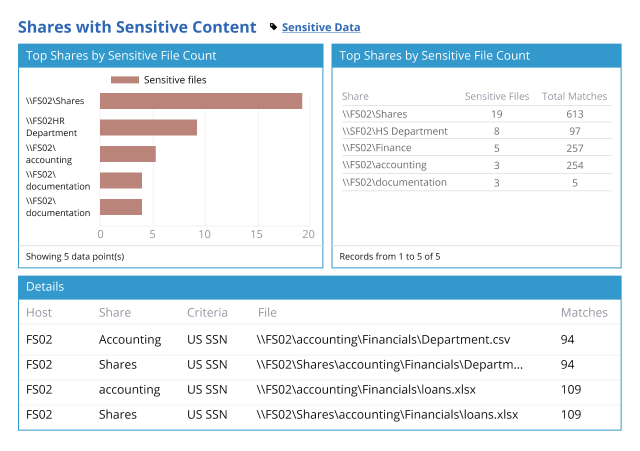
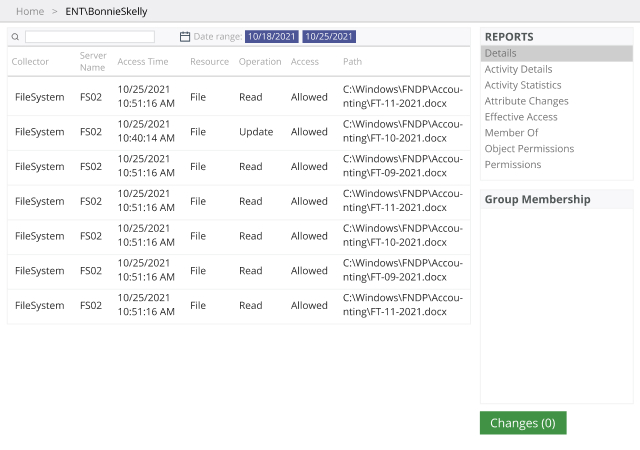
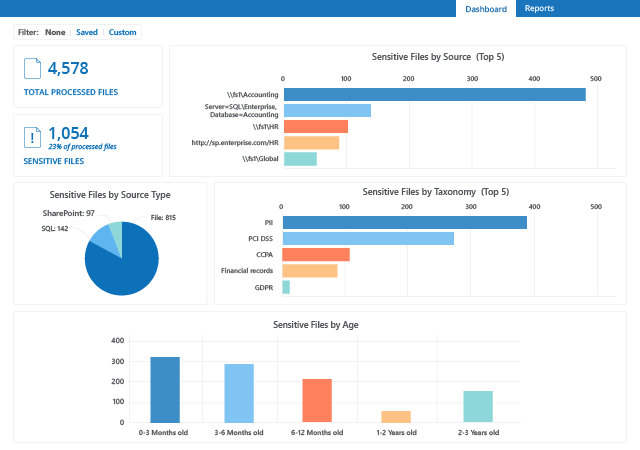
Which information is sensitive, regulated or business-critical? Is it overexposed or otherwise at risk? How big is that risk? By answering these critical questions, you can prioritize your data security efforts based on your risk profile and business needs.
Minimize security risks by limiting access to sensitive data
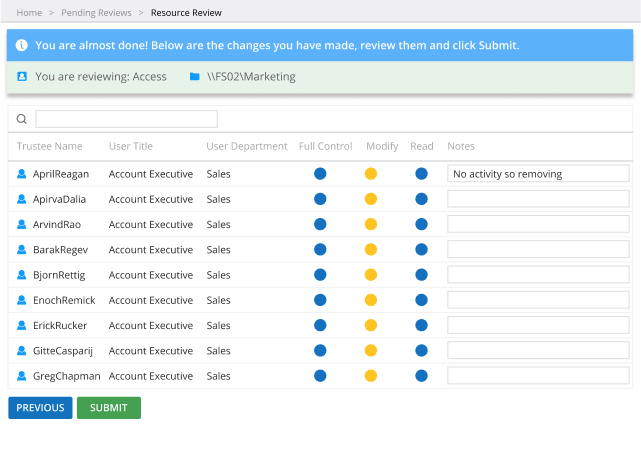
To reduce the risk of cybersecurity incidents, organizations need to understand who has access to what in their environment and granularly manage access to sensitive, regulated and mission-critical data.
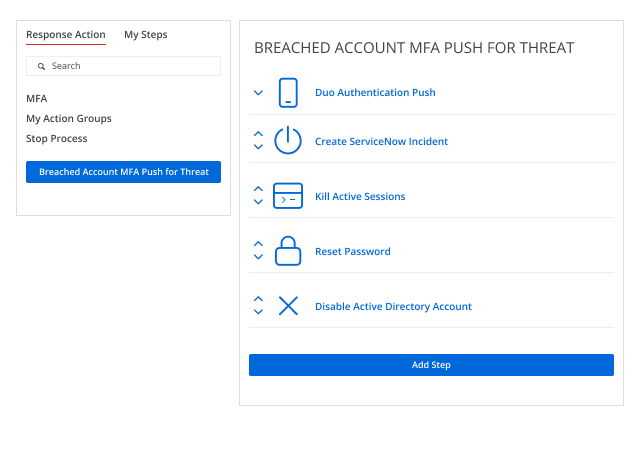
Curb the impact of security incidents
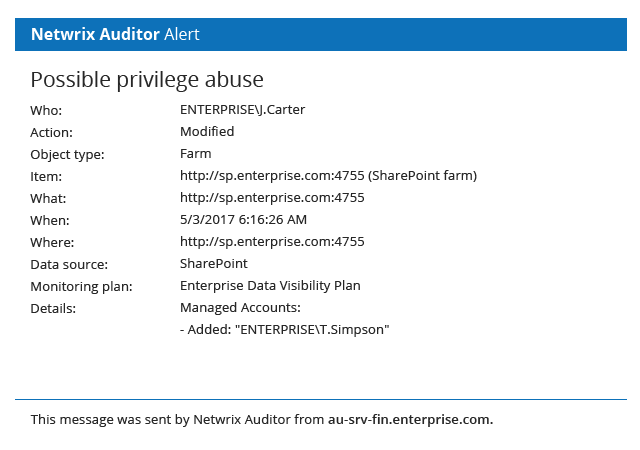
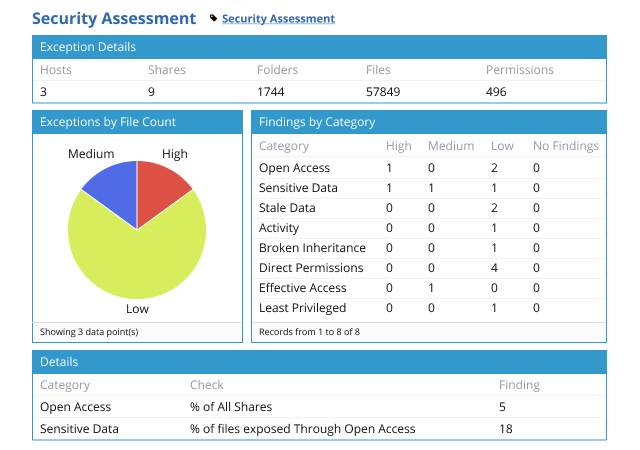
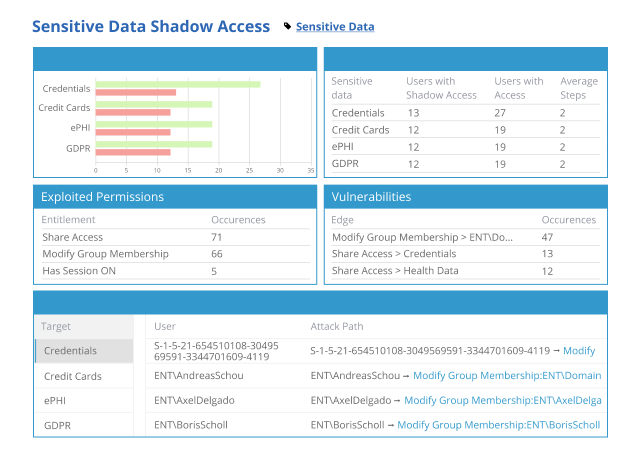
Speed incident response and contain insider threats more effectively by promptly spotting abnormal user behavior and access policy violations that threaten data security with continuous monitoring of data access and privilege escalation attempts.
Speed recovery from security incidents
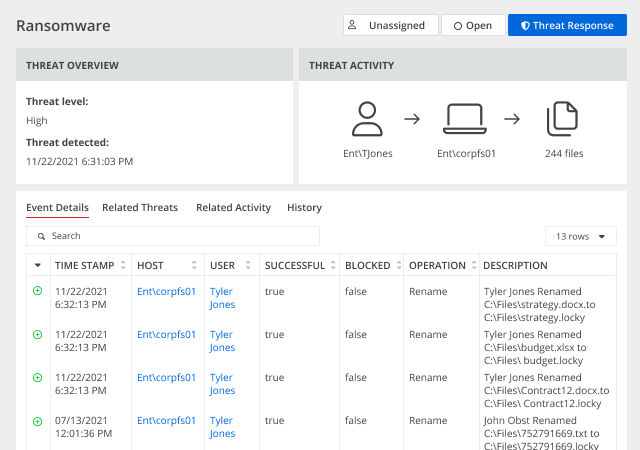
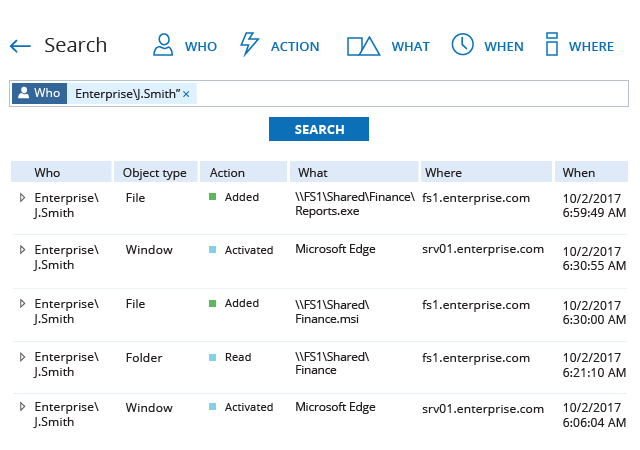
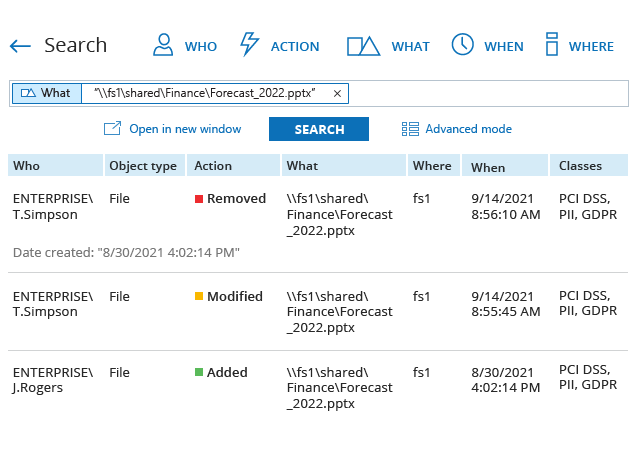
Recover from a security incident faster with details about how the incident unfolded, what data was affected and how the malicious actor obtained access to it. Revert quickly to a secure state and incorporate lessons learned into your data security strategy.
Gain control over your data and the ones accessing it
A robust risk management strategy heavily relies on understanding what types of data an organization possesses and who has access to it. Having a clear understanding of these fundamentals enables security professionals to apply adequate security measures and ensure company-wide data access governance.



_1640080035.jpg)
_1640002586.jpg)