Spot threats in real time and proactively block critical events with Netwrix StealthINTERCEPT
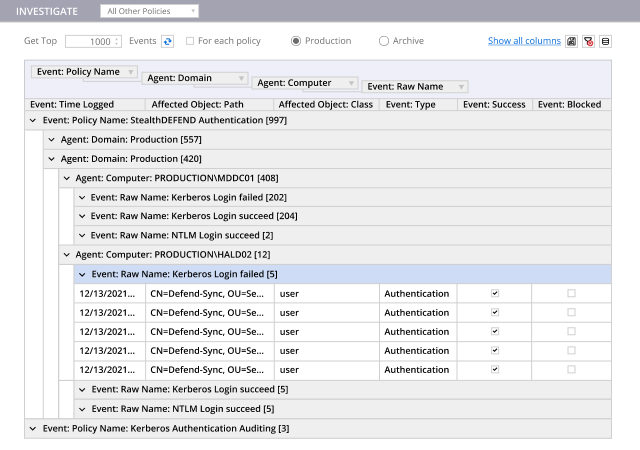
Organizations struggle to spot threats in their IT ecosystems before it’s too late. Indeed, industry analyses reveal that attackers often lurk inside corporate networks for nearly a year before being discovered — and the longer it takes to spot a threat, the more costly the resulting data breach can be. Netwrix StealthINTERCEPT alerts you to suspicious or risky changes, authentications and other events in real time, so you can prevent them from turning into full-fledged breaches that land your organization in the headlines. Moreover, it empowers you to block critical events from ever happening in the first place.
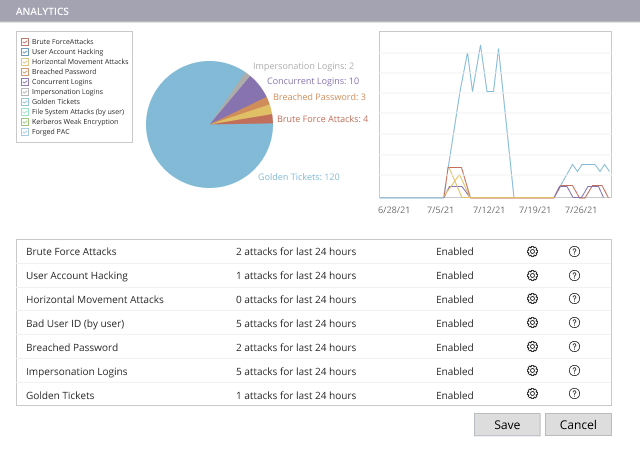
Get true security intelligence — in time to make a difference


.jpg)