SharePoint Security Tool from Netwrix
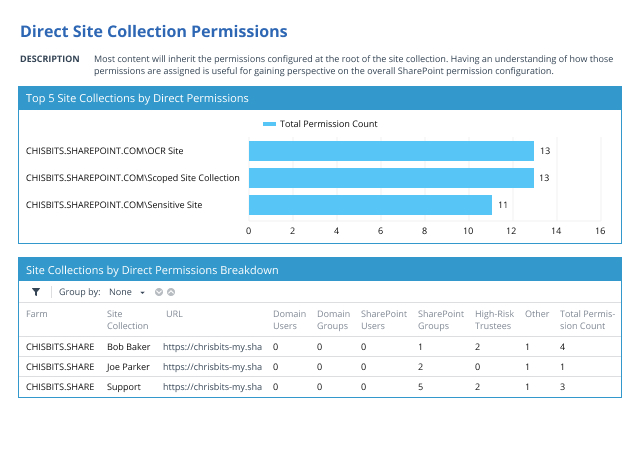
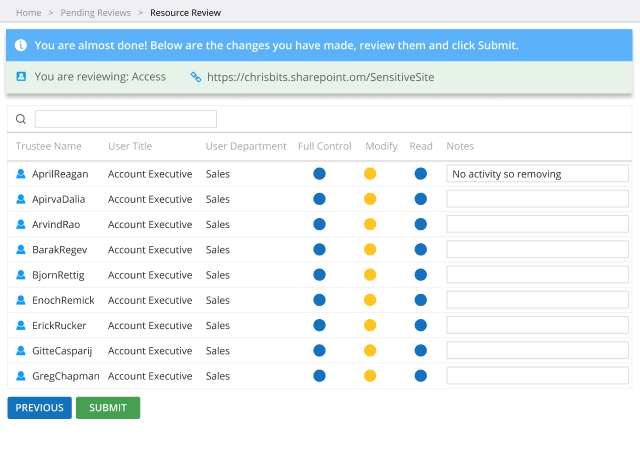
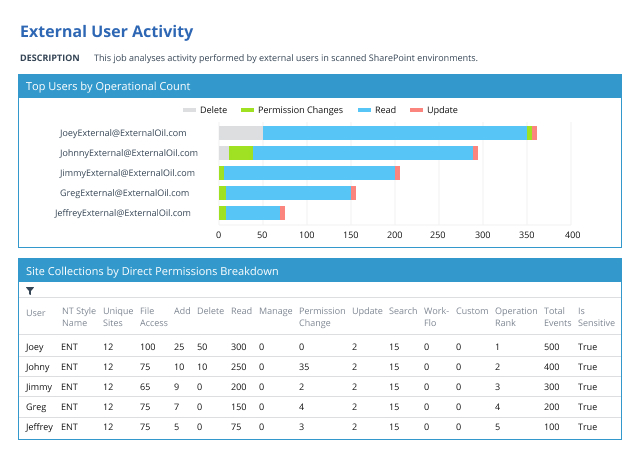
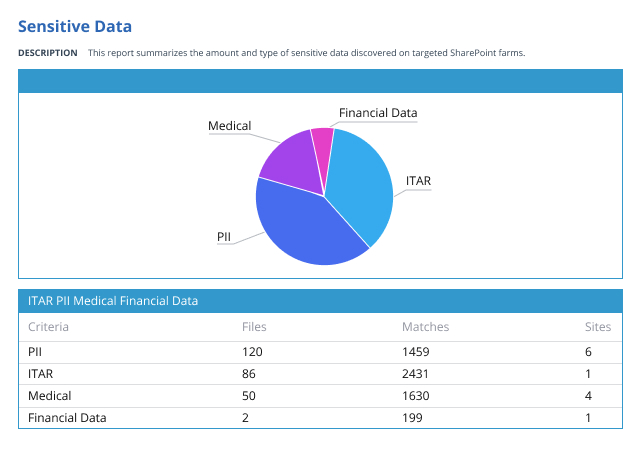
Every day, your users create, access and share massive amounts of data in your SharePoint Server, SharePoint Online, OneDrive and Microsoft Teams. Netwrix Enterprise Auditor (formerly Netwrix StealthAUDIT) for SharePoint enables strong security and governance across all these platforms, empowering you to establish and maintain a least-privilege model, close security gaps, control external sharing, monitor user activity, and more.
Strengthen security and ensure compliance with an advanced SharePoint security audit tool
Netwrix Enterprise Auditor (formerly Netwrix StealthAUDIT) for SharePoint is a powerful SharePoint security tool that empowers you to protect the sensitive data that your in-office and remote workers store and share in SharePoint, SharePoint Online, OneDrive and Teams, as well as easily prove your success to auditors.