Minimize the Risk from Admin Activity with Privileged Access Management Software
Gain confidence by discovering privileges across your systems
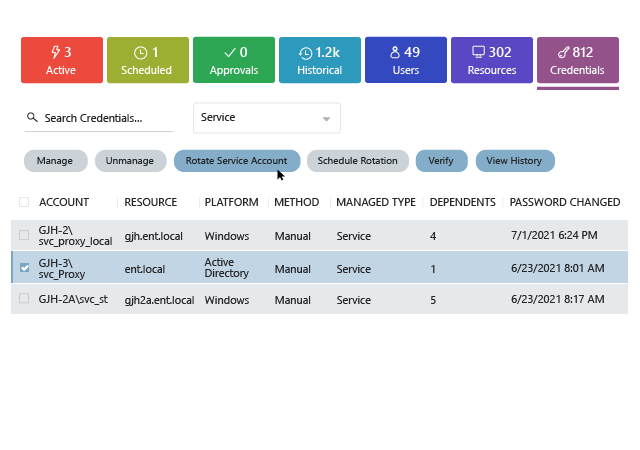
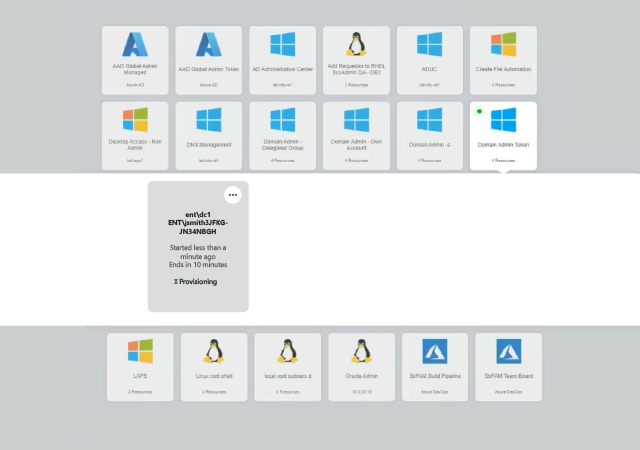
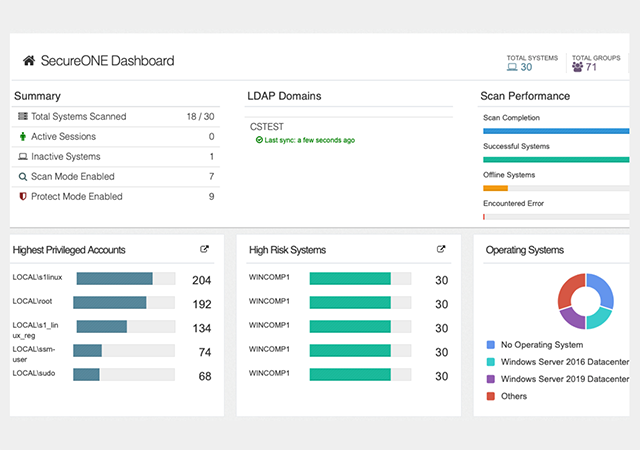
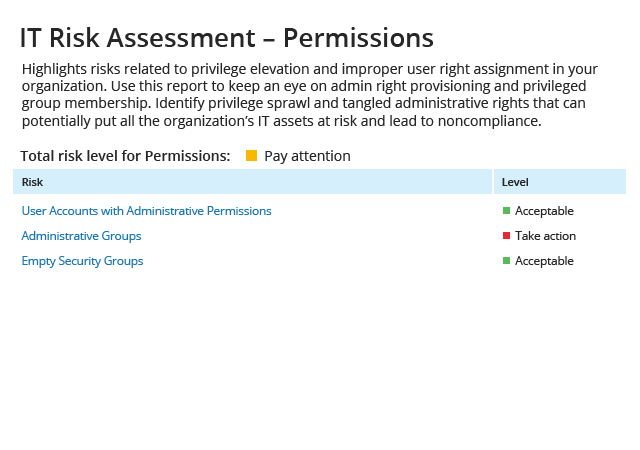
Rapid technology advancements and high user expectations mean that new systems and applications are constantly being added to IT ecosystems — and new privileged accounts are being created all the time to manage them. Indeed, there are often so many privileged accounts that today’s overburdened IT security teams lose track of them. But how can you ensure the security of privileged accounts you don’t know about?
Slash your attack surface area by removing standing privileges
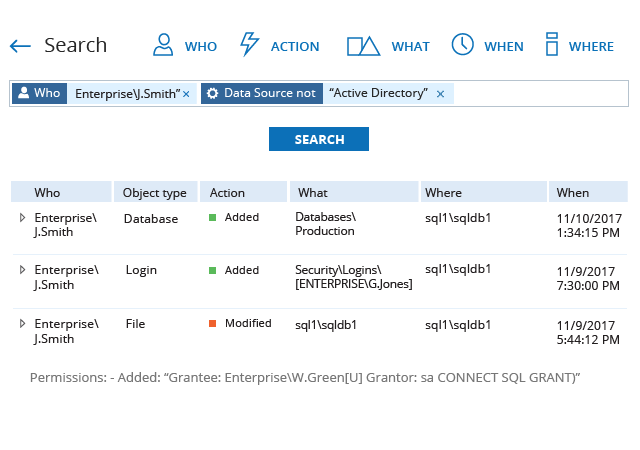
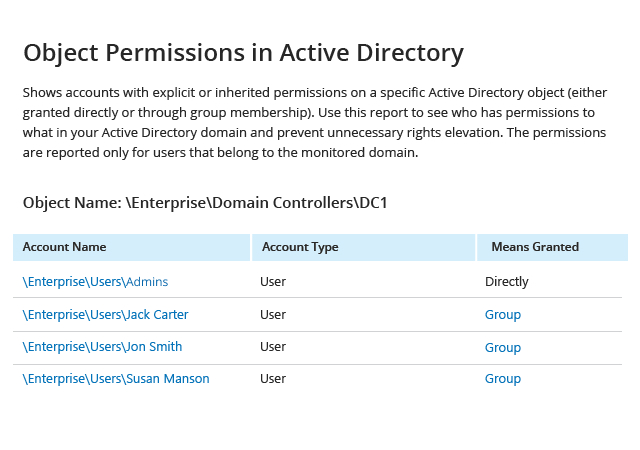
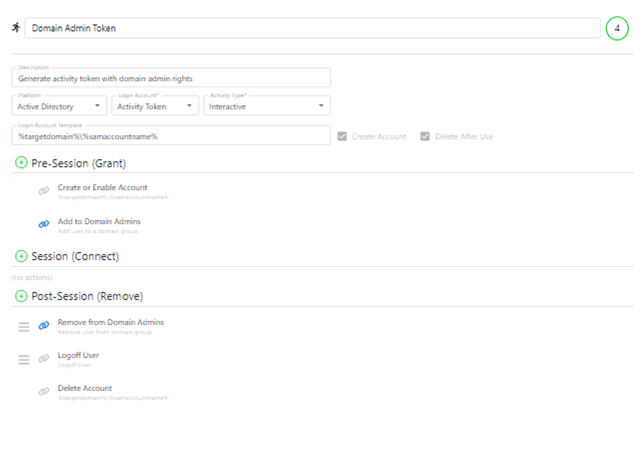
Because privileged accounts are so powerful, a single misuse or compromise can lead to a data breach or costly business disruption. Even if you keep privileged credentials in a vault, the accounts still exist and can be compromised by attackers or misused by their owners. In addition, common administrative activities leave behind artifacts that attackers can exploit and malware can use to propagate. How do you know that privileged activity is not putting your organization at risk? With the Netwrix platform, you can protect your organization with strong governance and access control.
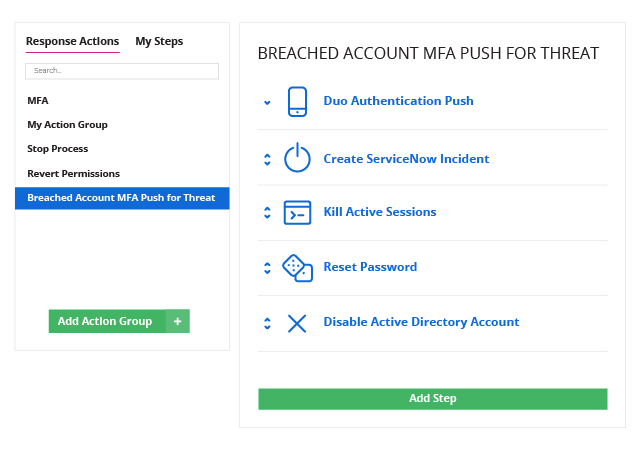
Minimize the impact of security incidents involving privileged activity
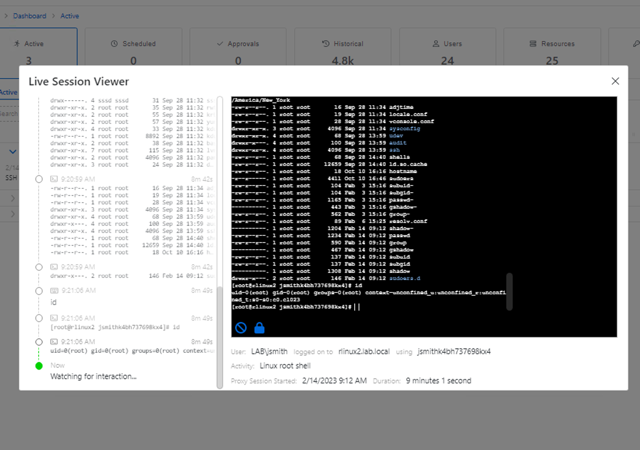
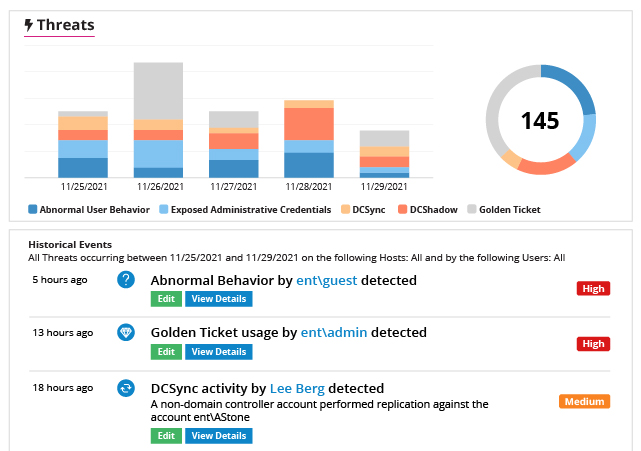
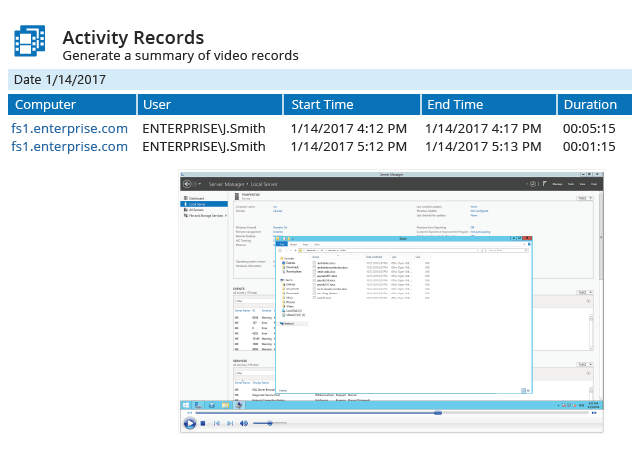
Gaining access to a privileged account drastically amplifies an attacker’s ability to cause damage and cover their tracks. Reduce your risk by detecting and responding to suspicious privileged activity faster.
Improve team performance while enhancing security
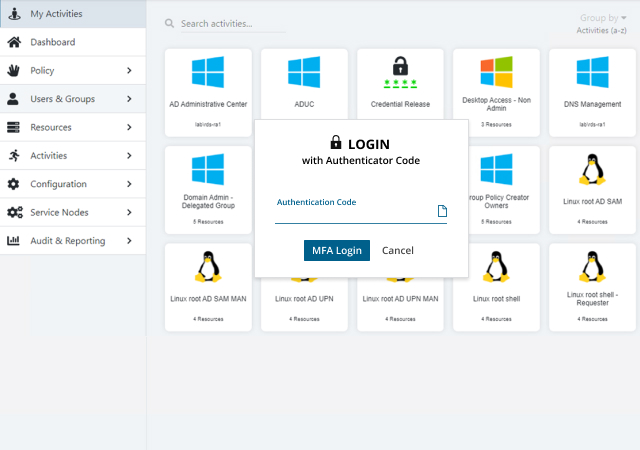
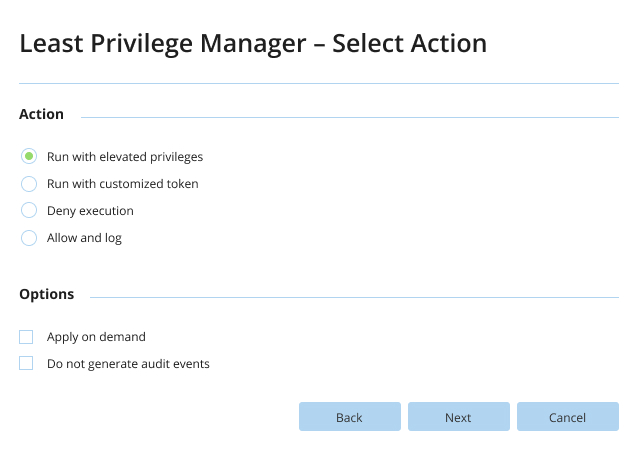
It is a common perception that privileged access management is hard and costly. But it doesn’t have to be! Improve security without overburdening your team with a solution that is easy to deploy and maintain and that slips seamlessly into your current workflows.




.png)