NETWRIX PRIVILEGE SECURE FOR ACCESS MANAGEMENT (formerly Netwrix SbPAM®)
SECURE PRIVILEGED ACTIVITY WITH
JUST-IN-TIME ACCESS
JUST-IN-TIME ACCESS
Minimize security risk related to privileged access, enhance team performance and pass audits with less effort
Slash the risk of compromise or misuse of privileged accounts
Shrink your attack surface
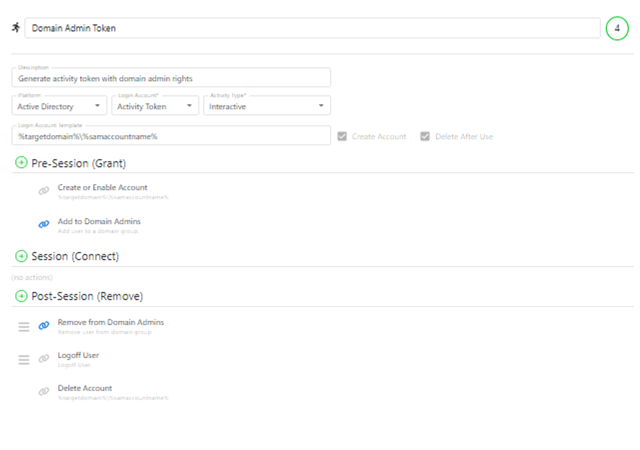
Kill standing privilege by eliminating standing privilege. Instead, create temporary accounts with just enough access to perform the task at hand and remove them when the job is complete.
Control sessions in realtime
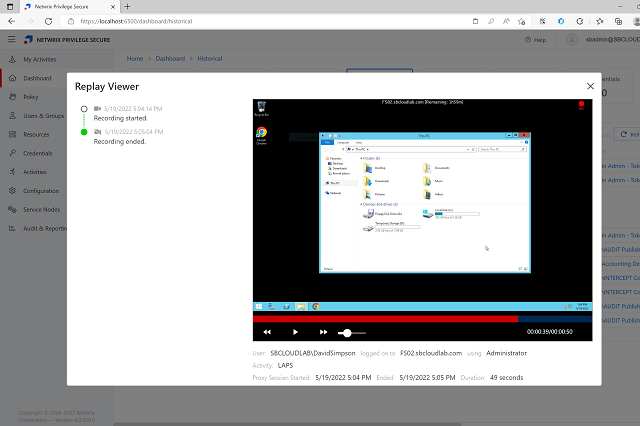
Raise the bar of accountability by controlling sessions in realtime through monitoring of admin activities, recording of all SSH and RDP keystrokes and local command execution, and the ability to review and search recorded sessions with granular metadata search for live and recorded sessions.
Safeguard service accounts
Protect service accounts by rotating their passwords from one place; receive an alert if the process is disrupted, so you can pause it and roll back any unwanted changes.
Respond to auditor’s questions painlessly
Be prepared to quickly and definitively show who approved each privileged session, exactly what activity occurred during it, and whether any local groups or critical files were changed.
Bring your own vault®
Secure privileged accounts on your terms. Integrate Netwrix Privilege Secure with your current vault or use ours to store any privileged credentials that need to exist.
Secure local Administrator accounts
Enhance the protection of local Administrator accounts while maintaining convenience by integrating Netwrix Privilege Secure with LAPS.
Facilitate existing workflows
Empower your team to keep working the way they are used to, but more securely, by integrating Netwrix Privilege Secure for Access Management with your existing internal and third-party applications.
Enhance threat detection
Augment threat detection mechanisms by forwarding logs about privileged activity to your SIEM, where they are correlated with the information from other systems.
Regularly certify privileged access
Ensure compliance and boost security by regularly verifying the legitimacy of each user’s privilege.
Automate clean-up to minimize your attack surface
Further reduce security risks with automated purging of Kerberos tickets and disabling of RDP.
Ensure privileged access is authorized
Ensure all privileged activity is legitimate and performed by a trusted user by approving or denying requests for privileged access.
Advance toward Zero Trust
Validate identities by enforcing contextual multi-factor authentication (MFA) each time an admin initiates a privileged session.
Protect database admin accounts
Supports full identity and privilege orchestration capabilities for multiple database platforms.
Gain privileged access insights instantly
Access out-of-the-box and customized reports, as well as favorites through an intuitive dashboard.
Discover and onboard unmanaged accounts
For each supported platform, a built-in scanner lists all domain and local accounts with associated privileges. New controls make it simple to identify and onboard unmanaged privileged accounts.
Netwrix Privilege Secure for Access Management
Netwrix Privilege Secure for Access Management enables you to eliminate standing privileged accounts. Leave no chance for compromise or misuse of privileged accounts.
Success Story
Read how Eastern Carver County Schools maintains least privilege access for IT admins to secure data of 9,300 students.

How is Netwrix Privilege Secure licensed?
Netwrix Privilege Secure is licensed by the total number of users that need to interact with the product. Licensing is simply by the number of users that need to log in and use the product. The license includes all features with unlimited platforms, unlimited managed accounts, and unlimited managed resources. Pricing includes full API access and comprehensive deployment options for fully redundant architecture.
How is Netwrix Privilege Secure different from other PAM solutions?
Unlike other band-aid solutions that simply vault your privileged credentials, Netwrix Privilege Secure removes your lateral movement attack surface by orchestrating privilege when you need it and removing privilege when not in use.
Can Netwrix Privilege Secure help me be more compliant with Cybersecurity Insurance requirements?
Yes, implementing a Privileged Access Management (PAM) solution such as Netwrix Privilege Secure can help an organization be more compliant with Cybersecurity Insurance requirements. PAM solutions typically include features such as multi-factor authentication (MFA) for privileged accounts, which can help prevent unauthorized access and protect against cyber threats. By using Netwrix Privilege Secure, you can demonstrate to your insurance providers that your organization has taken appropriate measures to secure your systems and meet industry-standard compliance requirements. This can potentially lead to lower insurance premiums and a greater level of protection against cyber-attacks.
Is Netwrix Privilege Secure easy to deploy?
Netwrix Privilege Secure can be initially deployed in less than 20 mins with full deployment less than 1 day.
How does Netwrix Privilege Secure make our environment more secure than other solutions?
Netwrix Privilege Secure reduces the lateral movement attack surface by removing privilege when not in active use and creating it on-demand with just enough access to do the job before removing it again at the end of the session. Additionally, Netwrix Privilege Secure includes session management tools for monitoring and recording privileged activities, for audit and forensics.
What is the danger of a compromised domain admin account?
In today’s AD-connected infrastructure, a compromised domain admin account gives an adversary the keys to the kingdom. Many organizations have an overabundance of users in the Doman Admin group; any one of these user accounts can be compromised via a plethora of lateral movement attack tools freely available on the internet. Lateral movement is an opportunistic type of attack that leverages privilege to move from system to system; Netwrix Privilege Secure prevents these attacks by removing privilege when not in use.